Inspired by all the Threat Hunting going around lately I’ve tried to apply it towards Pastebin posts, with the question: “What cyclical activity can I find and what does it revolve around?”.
There are certain limitations/issues which largely limits the possibility to detect malicious traffic:
- The pastebin API does not list untracked posts (C&C traffic naturally should use those)
- Pastes made as a guest are hard to find a cyclic connection between.
With those limitations in mind I performed a lightweight analysis which consisted of:
- Track all posts made by users and group analysis of posts by each of the user.
First some scripting to fetch posts from the feed, cyclic.py and dbcommands.py.
Then another to analyse the results, analyse.py.
The analyse.py script will iterate through the posts from each user, if one user repeatedly make posts within the same interval not outside of a decided error margin we see it as a cyclical activity.
I’ve tried running the analyse script with different options, setting the error margin in either direction one minute and require at least 10 consecutive cyclical posts seems to gain a high true-positive ratio.
Starting out with one of the most obvious one, the user releasemaster creates a new post each minute:
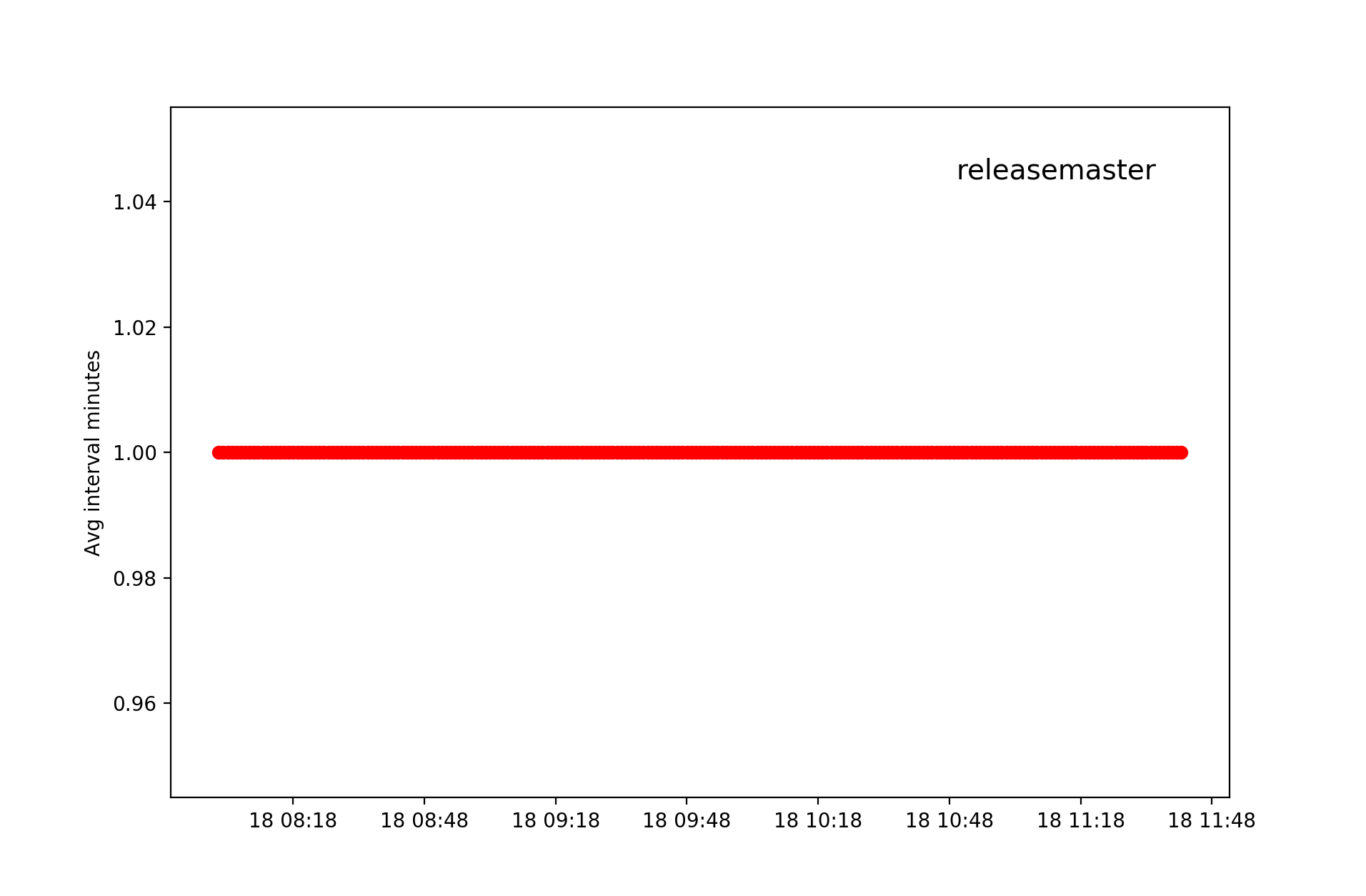
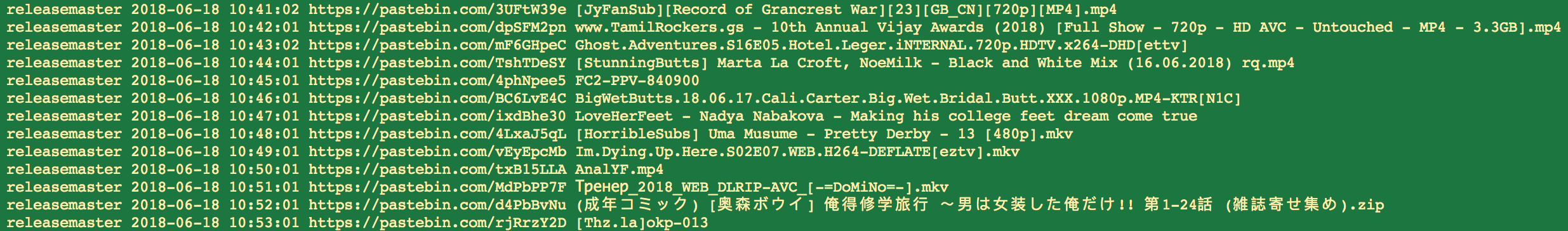
Judging by the username it’s not hard to guess that this bot is related to the Warez scene, looking at the titles of the posts confirms this:
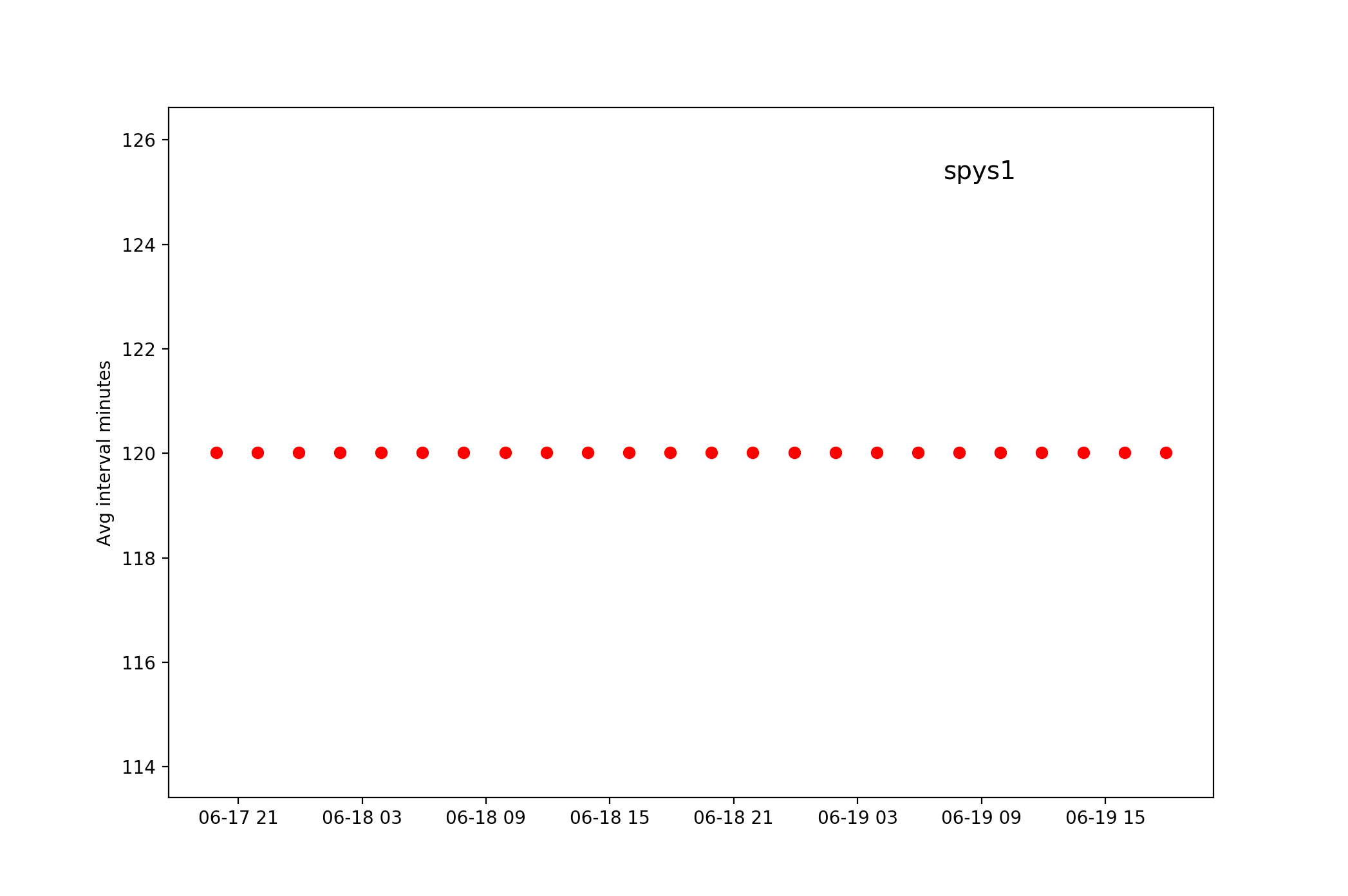
Then there’s another user named spys1 posting proxy lists every second hour:
The last one is a bit unexpected from a user named falion which is a character in the game Skyrim.
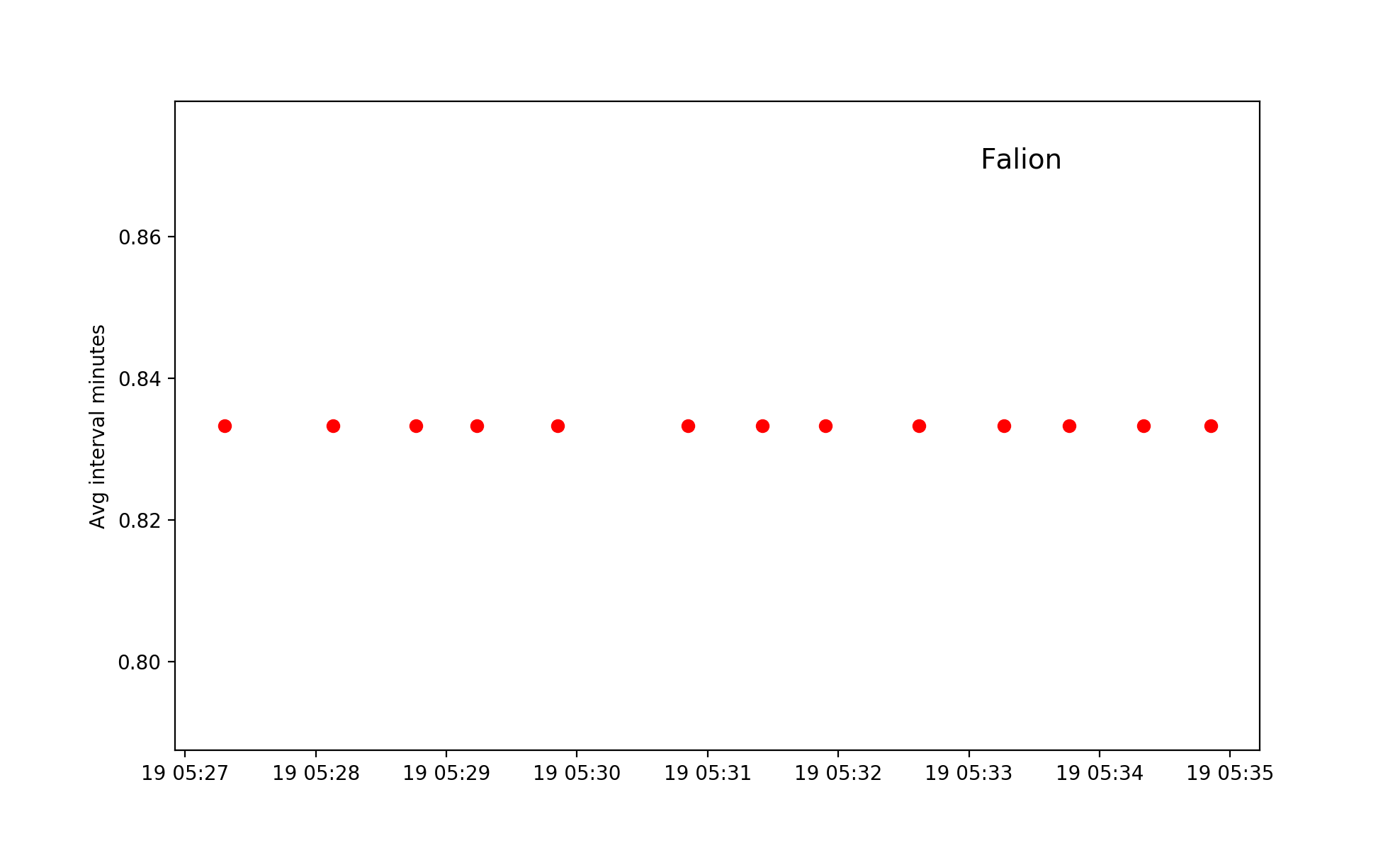
The activity is not completely cyclical, it has however been included as our error margin is very high when events happens very close to each other. I do however believe this is from an automated source as some subsets of the events are very cyclical.
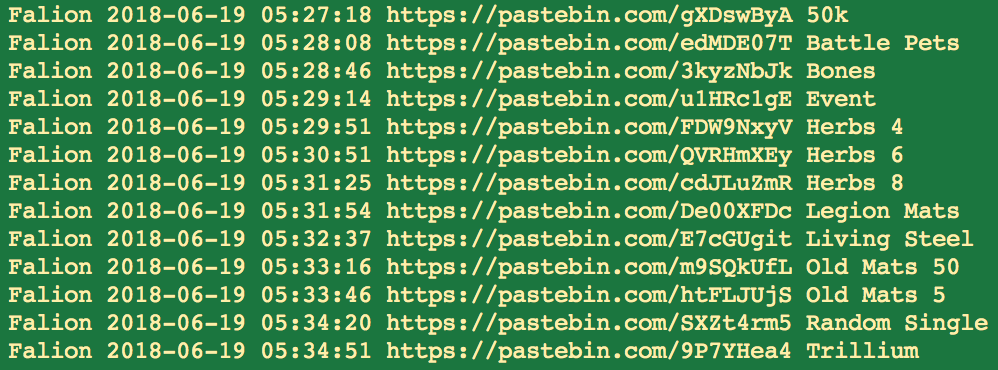
The posts contents seems to be some sort of logging from the game, example:
To conclude this is a rubbish way to Threat Hunt, it may however lay a foundation to try this method on posts from guests and in the process make the analysis more advanced, maybe one can group posts showing different forms of strong similarities and perform cyclical analysis of them. Lets try!