This is a writeup of the Hacking Time reverse engineering challenge from this years CSAW ctf.
Given a .nes file and the challenges name lead to the conclusion that it’s a NES ROM. The emulator FCEUX proved to be of great help with it’s inclusion of a debugger and hex editor.
After running the ROM and been shown some gibberish text the following password box was shown:
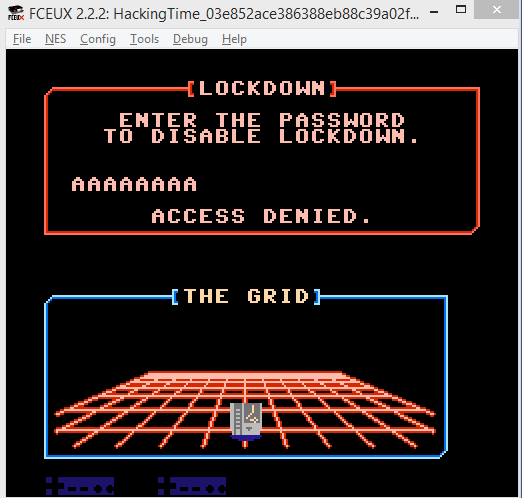
Viewing the memory with the hex editor one could easily find the input data starting at a memory location. I’ll placed a memory read bp there in order to find the subroutine where the validation was done.
Here’s the pseudo code of this function (A at the top is containing the input string element of index Y) :
A=A<<2
X=A
A=A<<1
PUSH A
A,X = MEM[3B]
A=A/2
X=A
A=A/2
MEM[3B] = A
POP A
CLEAR C
A = A+MEM[3B]
A = XOR MEM[955E+Y]
MEM[3B] = A
A=A>>3
X=A
A=A>>1
A=XOR A,MEM[9576+Y]
MEM[1E+Y]=A
Y++
IF Y!=24:
BRANCH TO TOP
Y=0
FAT_LABEL:
A = MEM[1E+Y]
IF A == NULL && Y==24:
Branch to good jump
Y++
IF A == NULL && Y!=24:
jump to FAT_LABEL
ELSE:
GOTO bad jump
So to summarize it:
Each character of the inputted data have some operations done on them, then the result of each character operated on must be 0.
One can create a nice looking keygen for this problem though I didn’t, in the end I just bruteforced each character to be the correct one as one can simply look at the memory to see the result of the operations.
The correct key was:
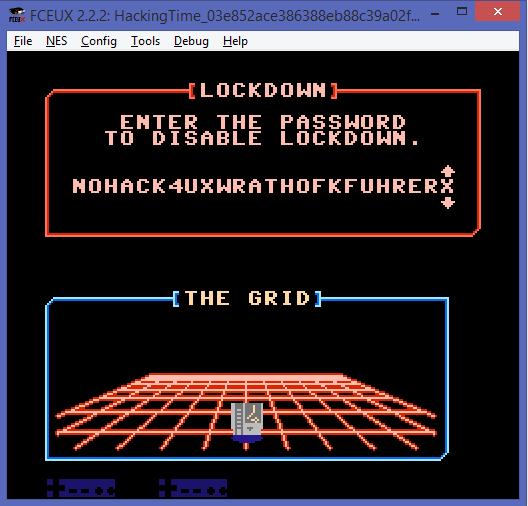
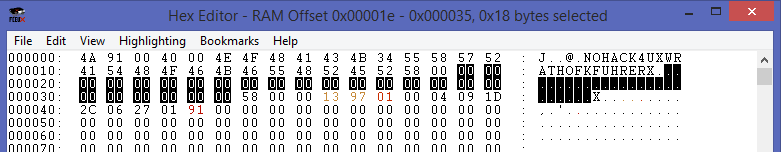
To verify that this is true we can look at MEM[1E+Y] where Y should be the index beetwen 0-23 (result of 24 characters).
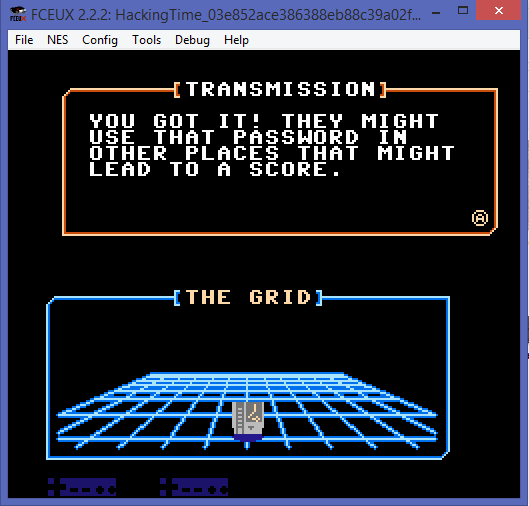
And be congratulated with this:
If you too want to dissasemble some NES ROMs the instruction reference will be of great use!